Background
Recently, I was having lunch with a young hacker. This person brought an interesting situation to my attention and asked me for my thoughts. The young hacker worked for a research and consulting firm. While working at that firm, this person, on their personal time, found an issue in a popular product/device. The hacker explained to their manager that they had discovered an interesting issue and were looking at it. Around the same time, that young hacker accepted a new job at a different firm. During the course of exiting the previous company, the hacker was told by their manager that the firm “owned” the vulnerability. The young hacker accepted that to be the case without consulting an attorney or someone with knowledge of contracts or employee/employer relations.
This firm regularly allows people to headline their findings as long as the firm name is associated with the research/find, which, as far as I know, is relatively standard practice. The ownership of the vulnerability, is, in my opinion, that of the person who finds it or the firm that pays for it to be found. Now, when I say that, my meaning is that if a firm pays me to do a pen test and I find a vulnerability, as far as I am concerned, they own it. I caveat that a number of ways, however, because 3rd party product testing opens questions and doors to other legal issues. But, for the sake of this discussion, let’s just simplify it and say that if you pay for it, you own it (caveats not included but implied). Since the vulnerability was discovered on this person’s personal time on a product/device they owned, I am of the opinion that this person owned the vulnerability and the firm, fraudulently represented that they owned the vulnerability.
If there was a contractual agreement that any vulnerabilities found at any time would be property of the company, that would need to be called out. Also, there are so many issues with contract clauses like that and all the precedence in the field for this not being industry standard, I believe would invalidate that. And, is a vulnerability intellectual property? Personally, I do not believe it meets the standard for intellectual property and I am not a lawyer. Any lawyers out there have an opinion on whether or not a vulnerability (0 day) can be considered intellectual property? So, question one is ownership. Who owns this vulnerability (is it IP, is it possible to contractually pass ownership, etc.)?
Things get a bit stranger as time passes. The vulnerability seems to have been used for further research as an entry point to perform a bunch of “stunt hacks” against the product/device. I am basing this on a recent communication from the young hacker where they outlined a talk that is going to be given that appears to be based on their initial find. So, subsequent work must have been done to go from the original vulnerability to full on developed stunt hacks of the product/device. However, the young hacker was not involved in any of that work. The original vulnerability is being used as the entry point. So, what we have here is a situation where none of the subsequent work could have been done without the original vulnerability. And we have the original finder of the vulnerability no longer involved at the company or involved with the research.
The company has developed research and is using this as a talk that will get them marketing/publicity and the people who present it will be viewed as the de facto originators of the vulnerability and subsequent research. The young hacker is not mentioned nor has there been any attempt to discuss joint presenting or attribution. In my experience, this runs completely counter to the spirit and code of what we do. And, let us assume that the first question of ownership returns as, the company can own the vulnerability, does that somehow negate the ethical/moral responsibility to give proper attribution? When I look at this, I am disgusted that the young hacker is not being given attribution and is not involved in any of the follow-on decisions of the use of the original vulnerability. So, my second question is what is the standard for attribution?
Legal Precedence
I reached out on both Twitter and LinkedIn to my network asking if there are any relevant legal cases that have ever been argued regarding vulnerability research, exploits and intellectual property. Or, is there any legal information that provides guidance on attribution in the field of information security research. Or, should we look to something like university research for a standard? Unfortunately, I did not receive any definitive answer. That being said, I found on legal “opinion” in an online forum that talks conceptually about these things.
In the following post, Kate Vershov Downing, who identifies herself as an IP Attorney, discusses these topics. Some of the language is a bit confusing and she intermingles some infosec terms but the gist of the post is relatively straightforward. I reached out to her on LinkedIn with an InMail but did not receive a reply.
The concepts that she covers tend to be around torts, intellectual property and assertion of property rights. The issue I have is that she does not seem to differentiate between a vulnerability and an exploit. And, as we know, there is a big difference. Many good bug finders are not exploit writers and many good exploit writers are not good bug finders.
Ownership of Zero Day Vulnerabilities and Exploits
So, if we look at the idea of property as I understand it, if there is nothing to own, there is no property. A vulnerability exists in property that is owned by a 3rd party (the manufacturer owns the design and in many cases, the code that you “use” for software). If anyone could claim “ownership” of a zero day vulnerability, the original equipment manufacturer/owner has the best, and, in my non legal opinion, only real case to claim ownership. That being said, a vulnerability has value. Think about a researcher in the field of chemistry. They discover a new element. That researcher has no ownership of the element but they have the ability to name the element and to always be attributed with the “discovery” of said element. They did not create anything but they discovered something so they should be the one given attribution. If they were working at a university or research lab, that university and lab would be given attribution as funding and supporting the research.
An exploit however is a very different thing. An exploit may use a vulnerability as an entry point or it may be the only thing needed to get an exploit to work. That being said, more often than not, a great deal of work goes into making an exploit work. Time, effort and expertise goes into crafting a working exploit. There is a great deal of intellectual property created. There is no question that a developed exploit has value. And, it seems to me that is relatively straightforward that this is intellectual property.
Standard for Attribution
What is the current standard for attribution in the information security field? Prior to my lunch with the young hacker, I thought there was a relatively well accepted, unspoken rule for folks who regularly do information security research and work for known firms or themselves.
When working on a client related matter, generally, the client owns the vulnerability and determines if disclosure is something that will be done. Oftentimes this is done in concert with the client. I have dealt with clients who want to disclose as issues are found in their vendors’ products.
When a researcher is working on company time or paid research for the company, attribution is generally shared. The company will work with the researcher to aid in the process of disclosure, marketing etc. and it is a joint effort with the researcher still getting top billing.
When a researcher is not on company time or paid research and finds an issue, they are free to choose what to do with it. Some of them report directly to the companies while others sell vulnerabilities, develop exploits or do other things depending on their own position. I have known some who simply hold on to the findings…..saving it for a rainy day, so to speak .
But when I asked a few people about their opinions on this, I got wildly different answers. One person told me that they think companies should not give attribution to researchers if they are working for the company or on company time. Another person told me that researchers should always be top billed and should not include the name of the company under any circumstances.
Some of this can be easily included in contracts like employment agreements. However, it is difficult to talk about attribution of something with no real intellectual property value. Many companies make employees sign IP agreements but, in the case of a zero day, that argument falls on its face. So, we need some different, equally explicit agreements around attribution of zero days and what happens in the case of separation.
Basic Lifecycle and Value of a Zero Day Vulnerability
To illustrate the lifecycle of a vulnerability let's look at the following graphs:
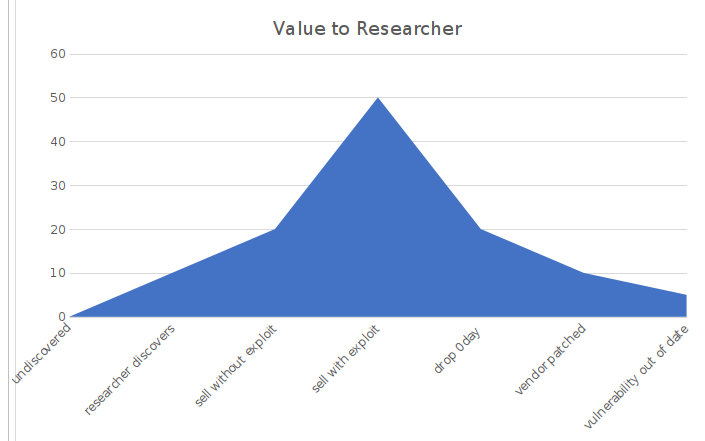
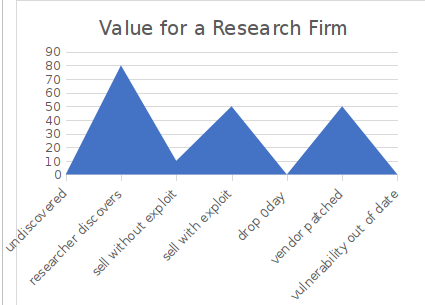
If we are looking at the value of a zero-day vulnerability relative to the position of the researcher or a research firm, we can see that they are not aligned. Because of this misalignment and the value to a firm over time, we are seeing an uptick in firms forcing their hands and working to limelight grab. I believe that, until there is a candid, realistic discussion between research firms and researchers, this will continue to be exacerbated.
Wrapping it up a Bit
If we draw this out, some vulnerabilities may have great monetary value. In the case of the young hacker, I am not sure the original vulnerability would have had much value but definitely some intrinsic value. That being said, the value increases exponentially for a firm that trades on research and uses this as a marketing tool. And the fact that the firm is not giving attribution for the find, lends itself to a story where they are depriving the young hacker of attribution for some reason. The only thing I can come up with is that they want all the glory for themselves. If that is the case and the “glory” of the initial find has some value, is that firm not denying the young hacker that value? And even more simply, if you think about the value for the young hacker being attributed with their find can have long term positive impact and giving attribution to someone who worked at your company at the time of the find and has essentially given the vulnerability to that firm seems that there must be some malice. If this firm is maliciously withholding or depriving the young hacker of monetary value and using it for themselves, is that conversion ( https://en.wikipedia.org/wiki/Conversion_(law))?
I am very interested to hear if there is case law on vulnerability as intellectual property and what the industry thinks about ownership and attribution. But what I am really interested in is whether or not the aforementioned firm in this scenario will step up and do the right thing by giving the young hacker credit where credit is due. Skip all the legal mumbo jumbo, act like a hacker and give attribution where it is due...
Where Anvil Stands
Opinion on Vulnerabilities - Not intellectual property. However, attribution of a vulnerability, even without exploit or POC or other IP, has material value. For a firm, there is inherent value in marketing that your firm/employee found a vulnerability. For an individual, the value is in personal branding which directly impacts pay, position, and long-term employment opportunities. Firms and researchers must work together to achieve an equitable balance. Things like post separation marketing support and representation should be worked out in advance.
A POC/Exploit or Code Written to Discover Vulnerability – Is intellectual Property. Ownership of these things depends on contracts. A fair contract should recognize work for hire standards. If a researcher is working on their personal time, this should define the personal ownership vs. firm ownership relationship. Firms who claim to support research should have real, enforceable rules about research vs. non-research activities.
Attribution – Matters. The individual researcher/finder always deserves attribution. Joint attribution with company should happen when contractually obligated ie. When paid work for client or paid research time. Contracts should be explicit in how attribution is handled and who is responsible for which part of attribution. If a find is made outside of paid research time, there should be an incentive provided to share attribution with a firm or to mention the firm as part of any announcement or marketing of the vulnerability.
O Day Market - Folks who traffic in 0 days – exploits (selling, brokering, buying) forfeit rights in exchange for monetary value or value of use. Researchers and 0 day firms are the main sellers. The criminal and government/ Intelligence Community (IC) are the two main players in the purchasing space. Anvil does not sell vulnerabilities or exploits.
About the Author
Chris Elbring is Managing Partner and CEO of Anvil Secure. Prior to founding Anvil, Elbring worked as CEO and CTO of a startup security software development firm, President of a boutique, regional security consulting firm, an independent technology and security consultant, Director of Software Development of a mobile, biometric firm and most recently as Senior Vice President of Research and Delivery at IOActive, Inc.

