By Vincent Berg
TL;DR
The Issue: Organizations need to be aware of looming deadlines for Post-Quantum Cryptographic (PQC) compliance.
The Solution: Anvil Secure is launching a free and open-source scanner that can determine whether SSH and TLS servers support PQC algorithms. This tool will help organizations with their compliance needs in a PQC future, and it can be downloaded from Anvil’s GitHub project page.
Background
The USA, EU and UK have all set deadlines for phasing out non-PQC algorithms completely between 2030-2035. Some of the big hyperscalers have also made moves in this direction, for example Google and Cloudflare. Given the size of their infrastructure and their control of client support for PQC-algorithms in the case of Google Chrome, these efforts have a massive impact on world-wide users. Basically, anything that is reachable via an up-to-date web browser and is running on top of modern hyperscaler infrastructure will switch to PQC-algorithms automatically when all the other hyperscalers migrate.
However, there are a lot of organizations with legacy software and hardware out there. These all need to, (depending on their risk appetite and relevant regulatory regimes), migrate towards using PQC-algorithms exclusively. The first step of such a process is possessing the ability to identify and discern non-PQC and PQC capable services on your network.
To help with this, Anvil wrote an easy scanner that can, for SSH and TLS services, quickly identify if these services support PQC support. Anvil has already started using this tool to help some of its clients with their journey towards a PQC future. By releasing it publicly, it is our hope it will provide more organizations with the means to get visibility on where they are in the PQC deployment processes.
Scanning
PQCscan has two scanning modes: tls-scan and ssh-scan mode. We will explain each mode below followed by some notes on the reporting mode.
TLS Scanning
TLS Scanning supports (as of the time of writing), identifying both hybrid and non-hybrid PQC algorithms. Only standardized algorithms are supported and experimental algorithms will not be identified. The current list of probes sent is as follows:
X25519MLKEM768 SECP256R1MLKEM768 SECP384R1MLKEM1024 MLKEM1024 MLKEM512 MLKEM768
To demonstrate the tool we selected the top 100 domains as ranked by Cloudflare Radar. We then modified the CSV file into a target list, and we assume every entry has an HTTPS server listening on port 443. We then used pqcscan to scan these domains and converted the report to HTML output.
$ cat cloudflare-radar_top-100-domains_20250620.csv | tail -n +2 - | cut -d ',' -f 2 | sed 's/$/:443/' > top-100-targets $ pqcscan tls-scan -T top-100-targets -o top-100-scan.json $ pqcscan create-report -i top-100-scan.json -o top-100-report.html
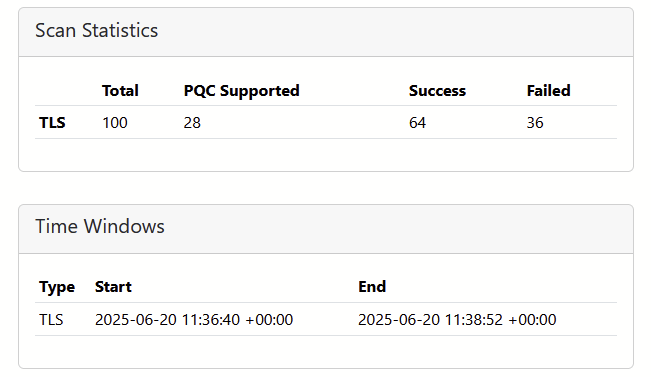
When opening this HTML file, we see that that of the 100 domains that we attempted to scan 36 scan attempts failed. Most often this is because there is no A or AAAA record for these domain names setup which simply means there is no website configured that could be listening on port 443 for these domains. For example, the domain a2z.com is associated with Amazon but it is part of their internal employee portal.
If we then look at the 64 successful scans, we find that 28 hosts actually support PQC algorithms. That is, from the top domains, close to 1/3 of the entire list. Or one could argue it is almost half of the successfully scanned domains. In other words, the domain that actually had a website configured on port 443 and was speaking TLS properly.
In similar fashion we ran a scan for the top 10,000 domains. That yielded a total of 1,386 domains that had PQC TLS support out of a 6,430 successfully scanned. Upon examination all of these seem to implement X25519MLKEM768 which is the most consistently and commonly deployed hybrid PQC algorithm that is out there.
SSH Scanning
PQCscan has two scanning modes: One is called tls-scan which was demoed above. The other one is called ssh-scan. This will start a SSH key exchange and then will filter against a database to display support for PQC algorithms by that SSH server. Similarly as with the TLS scaning mode a user can supply a target list or just a singular target. In the example below, let’s scan two commonly known public SSH servers as well as an internal network one:
$ cat > ssh_targets| 100.126.128.144:22 github.com:22 notexisting:55 $ pqcscan ssh-scan -T ssh_targets -o ssh.json $ pqcscan create-report -i ssh.json -o report.html
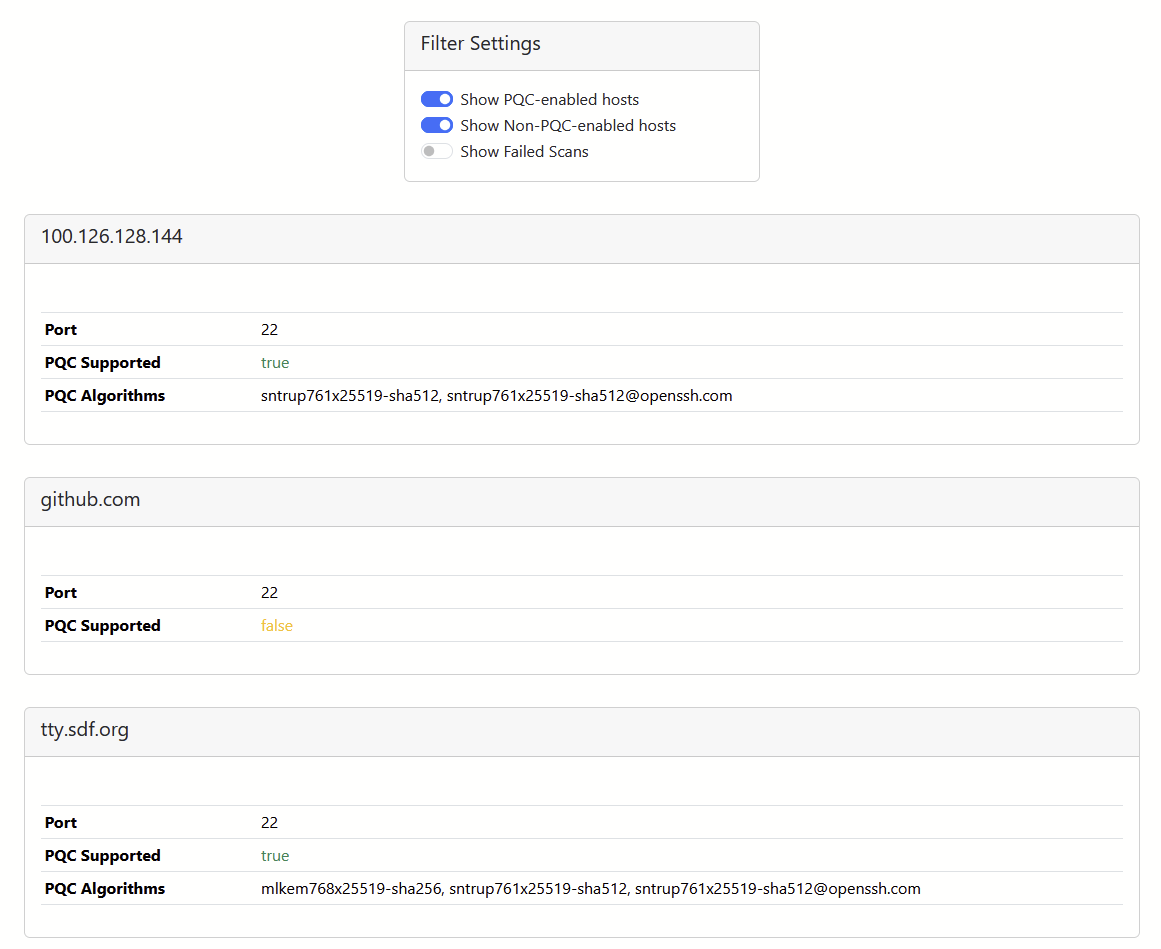
The following screenshot shows the SSH tab results page where you can filter on the results and get the list of algorithms that are supported by the scanned hosts.
Reporting
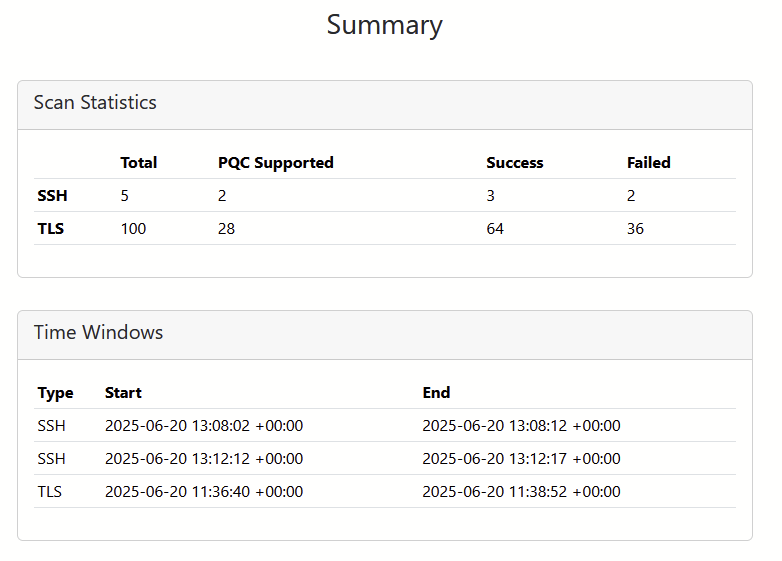
Reports of SSH and TLS scans can easily be combined into one HTML report. For each scan it will show display the time windows as well. Simply pass in all the scan output JSONs one by one to PQCscan as follows:
pqcscan create-report -i ssh1.json ssh2.json tls1.json -o report.html
This will result in something like the following:
More information
The scanner is a proof of concept and it currently only reports based on the reported capabilities by a service without attempting a full PQC enabled handshake. As Anvil continues to improve the tool with added support for more experimental algorithms and anticipated full negotiation tests of PQC algorithms, it is our hope that it will continue to assist you as you move to PQC compliance.
We welcome any and all feedback.
For more information please go to its GitHub page. It is licensed under the 2-clause BSD license and we welcome any and all feature requests, bug reports and otherwise suggestions. This can be done through GitHub or by emailing directly to gvb@anvilsecure.com.
About the Author
 Vincent Berg is the Chief Technical Officer at Anvil Secure. Vincent’s strong technical background and years of consulting experience drive his belief that technical excellence and professionalism should be at the core of everything we do at Anvil. As CTO, he guides research and technical content, while maintaining a client-focused approach.
Vincent Berg is the Chief Technical Officer at Anvil Secure. Vincent’s strong technical background and years of consulting experience drive his belief that technical excellence and professionalism should be at the core of everything we do at Anvil. As CTO, he guides research and technical content, while maintaining a client-focused approach.

